FIDO2 - TOTPRadius VPN Portal - Easy and secure access to corporate VPN
FIDO VPN Portal
Starting from v0.2.5 TOTPRadius provides new ways of connecting to your corporate VPN systems based on L2TP, such as Meraki Client VPN or Fortinet VPN . The new web-based VPN portal allows logging in using additional methods, such as FIDO Security keys, both in Passwodless mode (if FIDO2 keys are used) and using the keys as the second factor (allowing to use legacy U2F FIDO hardware), as well as Azure AD (Microsoft Entra ID) SSO via OAuth2 protocol.
Demos
The videos below show the user experience when using FIDO2 VPN portal in different configuration modes:2FA mode (without passwordless, makes legacy devices compatible with the solution)
Passwordless mode (only FIDO2 keys can be used)
The network setup and required firewall rules for different usage modes of TOTPRadius are described in this article. It is also important to set-up an FQDN and HTTPS web certificate for the VPN Web portal.
FIDO VPN Portal
Enable FIDO VPN portal in the Admin portal, General settings. The settings may look like shown below:
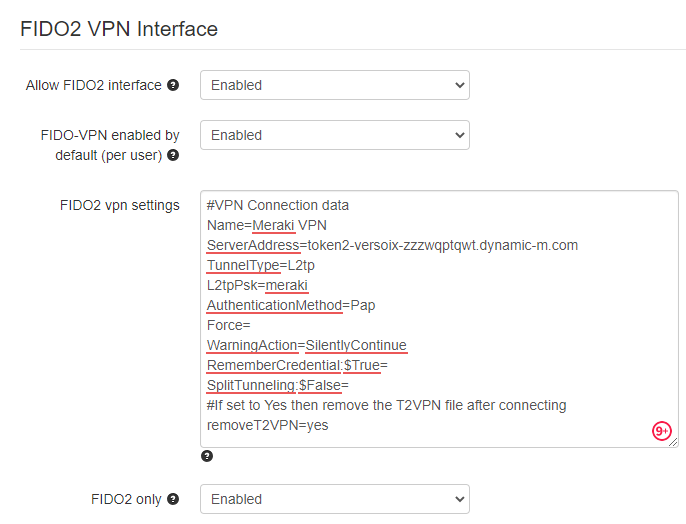
The settings shown on this example are explained in the table below:
|
Setting |
Description and possible values |
|
Allow FIDO2 Interface |
Enables this functionality. If disabled, the FIDO2-VPN Web Interface will not function at all |
|
FIDO-VPN enabled by default per user |
If this setting is set to Enabled, any user in your database or Active Directory will have access to the portal and can use this method to generate VPN connection files |
|
FIDO2 VPN Settings |
A configuration file template used to generate the connection files. The one on the screenshot above is showing the connectivity for Meraki Client VPN |
|
FIDO2 only |
If this setting is enabled, TOTP-based VPN access will be denied. Please note that this does not restrict Oauth2 login functionality (it has to be controlled separately) |
Advanced FIDO security keys settings
FIDO-VPN portal can support legacy FIDO devices (u2f) as well as Passwordless login if FIDO2 devices are used. FIDO2 offers full password-less authentication while FIDO U2F is designed to be used with a password as a traditional second factor only, therefore these settings cannot co-exist, only one of these options can be chosen. The settings are as shown below:
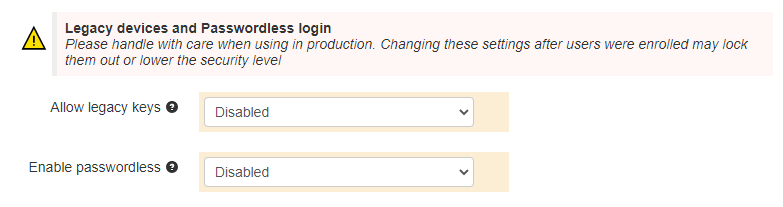
The settings shown on this example are explained in the table below:
|
Setting |
Description and possible values |
|
Allow legacy keys |
Allow using legacy U2F FIDO keys. If enabled, Passwordless method cannot be enabled or used |
|
Enable passwordless |
Allow Passwordless login method. It Is not compatible with legacy U2F FIDO keys option enabled and only FIDO2 security keys can be used. The system will check if the security key is protected by a PIN code or a fingerprint and prompt to protect if it is not the case. |
Once the settings are configured, you can test by visiting the configured FQDN. The interface is located in "fido2" folder (i.e. https://vpn-portal-fqdn/fido2/index.php)
Please note that versions prior to 0.3 allowed using only one FIDO2 key. More recent versions allow enrolling multiple keys per user.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
