TOTPRadius Network configuration
TOTPRadius – standard implementation diagram
The network diagram below is a recommended setup for a single TOTPRadius network (without VPN Web portal interface activated):
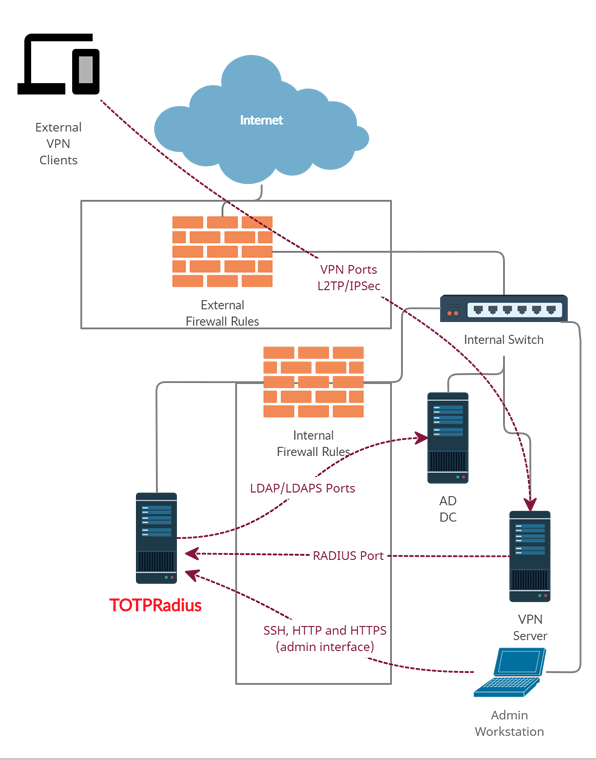
As shown on the diagram, access to TOTPRadius appliance is limited to 3 other hosts only:
- RADIUS port from your VPN server to TOTPRadius appliance (UDP 1812)
- LDAP or LDAPs ports ( TCP 389/636 )from TOTPRadius to your Active Directory Domain controller
- Access to the TOTPRadius management interface ports (SSH, HTTP and HTTPS – tcp 22, 80 and 443) is recommended to be restricted to admin workstations only
TOTPRadius – VPN Web Portal implementation diagram
If you wish to implement FIDO2/Passwordless or Azure AD (Microsoft Entra ID) Oauth2/SSO VPN access for your users (available starting from v0.2.5), there is an additional configuration required in your network layout. The web portal is running as a separate web server on the same virtual appliance, instead of standard https port (443) used for admin interface, the VPN web portal responds on port 9443. This port cannot be used directly for technical reasons, so has to be NATted to port 443.
The network diagram in this case will look like shown below:
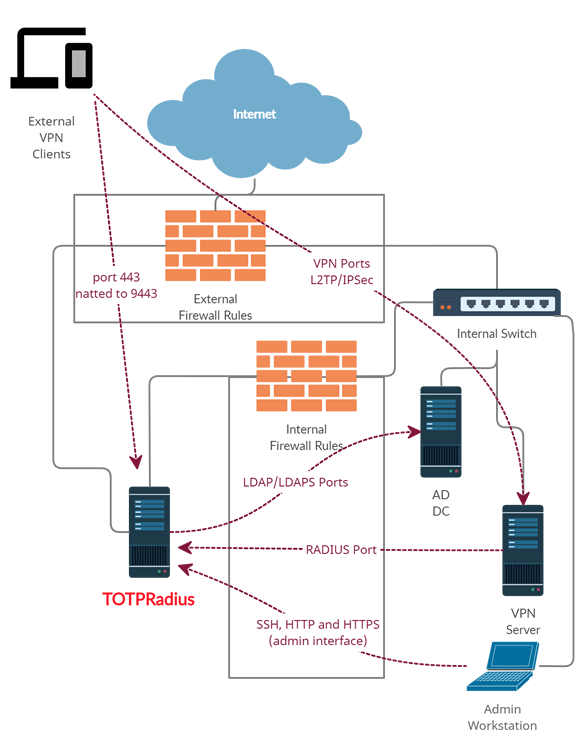
Below is the description of how such NATting can be configured using Meraki MX64 as an example.
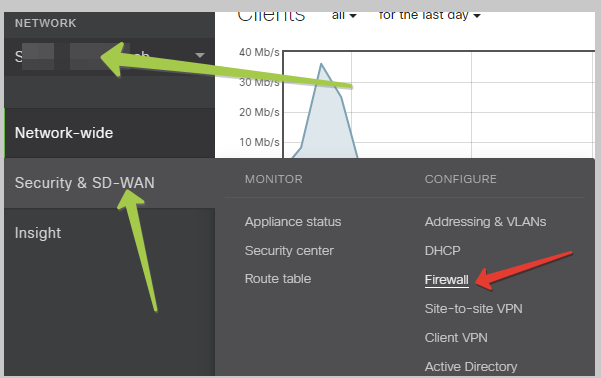
Login to Meraki Cloud Dashboard, and navigate to your Network. Then, navigate to “Security & SD-WAN” and select Firewall
Then, scroll down to 1:Many NAT section and add a NAT rule as shown on the example below
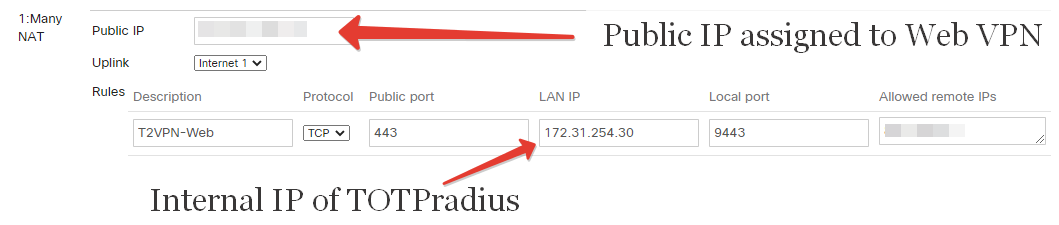
Once this is configured, the VPN Web interface should be accessible from public Internet via https://public_IP/ URL (where public_IP is the one you specified in the 1:Many NAT rule). Leave "Allowed remote IPs" empty or "Any" if you plan to expose the appliance without using any CDN. Please note that both FIDO2 and Oauth2 interfaces require an FQDN with a valid Web Certificate in order to function properly.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
