TOTPRadius - Remote syslog configuration options
System Logging Protocol (Syslog) is a way network devices can use a standard message format to communicate with a logging server.It was designed specifically to make it easy for administrators to monitor network devices, also review and manage those logs.
Starting from TOTPRadius v0.2.9, it is possible to send logs to a Remote syslog server. This can be configured in Settings → Remote syslog server
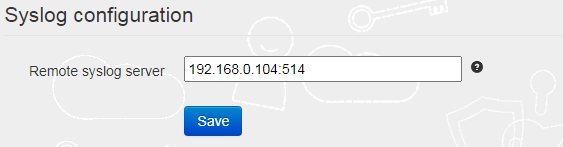
The syslog message contains information about user enrollment , authentication attempt, and admin’s activity . The server should be specified in IP_OR_FQDN:PORT format. Messages will be sent via UDP only. Set this value to "none" to disable the feature.
Message examples:
July 14, 2022, 02:33:56 token2 TOTPRadius; Radius authentication request from testuser01 ; Client IP: 192.168.0.104 July 14, 2022, 02:33:56 token2 TOTPRadius; Authentication attempt for testuser01 ; Return value: Reject July 14, 2022, 02:49:43 token2 TOTPRadius; Authentication attempt for testuser02 ; Return value: Accept July 14, 2022, 02:53:17 token2 TOTPRadius; Admin action: IP:192.168.0.104; admin/; table :users; action: insert July 14, 2022, 02:53:17 token2 TOTPRadius; Admin has added a user from the admin panel. Username: testuser03
Local syslog log file
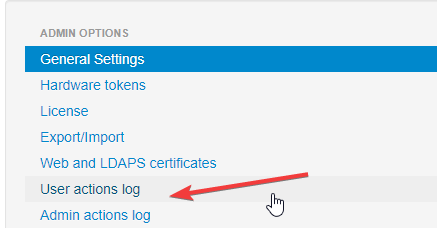
Even if a remote syslog server is not specified, a copy of syslog messages is kept on the appliance locally. This log can be accessed from Settings → User actions log
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
