TOTPRadius : MFA for SSH access to Cisco switches
Cisco switches do not natively support two-factor authentication, a third-party solution is required for this configuration. As a third-party solution we use TOTPRadius. This guide will document how to configure 2-factor authentication on a Cisco Catalyst 3750 Switch, using Microsoft Active Directory as the first factor and TOTPRadius Server as the second. This guide may be suitable for other Cisco Catalyst switch models as well.
The guide is based on the following components:
• Active Directory deployed on Windows Server 2016 ( ip: 192.168.99.10)
• Token2 TOTPRadius v0.2.6 with built-in free 5 users license( ip: 192.168.99.11)
• Classic or a programmable Token2 TOTP hardware token used as the second factor. TOTP compliant mobile apps can be used as well
• Cisco Catalyst 3750 series switch (management interface ip :192.167.99.77)
TOTPRadius configuration
Once the TOTPRadius appliance has been installed and initialized, configure the following settings on the General settings page:
► Set or generate a new Radius secret
► Set 'Allow initial login' value to zero
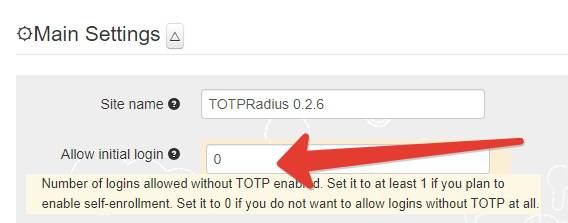
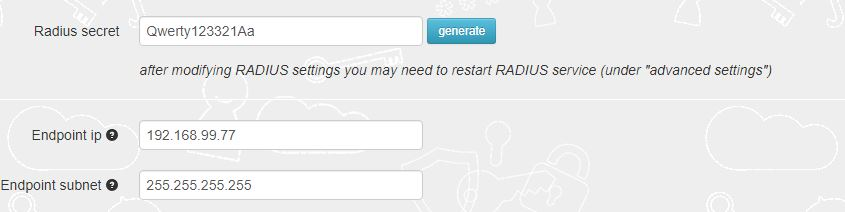
► [optional] In the Endpoint IP and subnet fields specify the parameters of your Cisco Catalyst 3750 Switch (192.168.99.77)
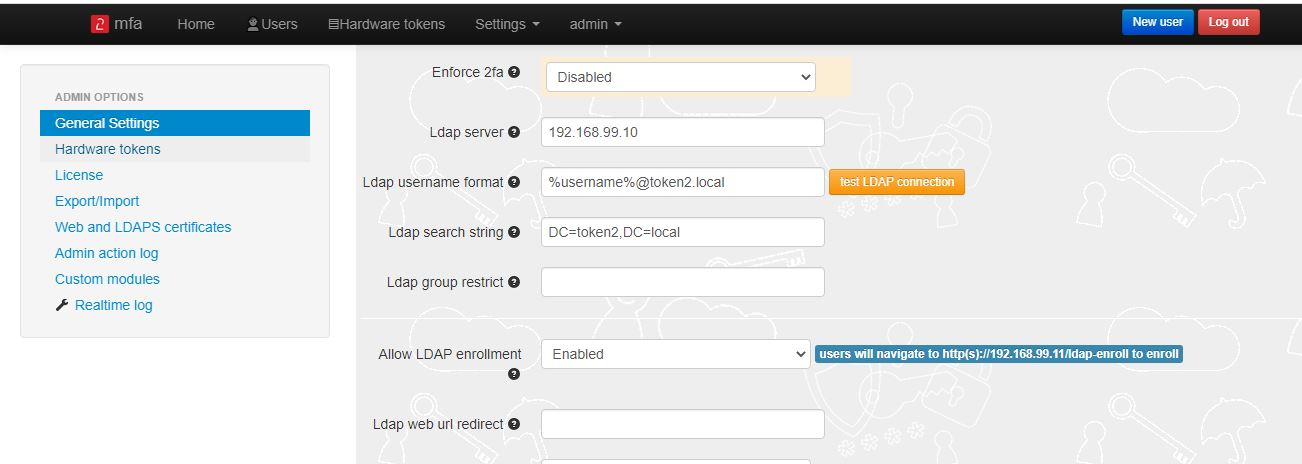
► Set LDAP as enabled
► Specify the LDAP server IP/FQDN (192.168.99.10) and the format of the username
(%username%@domain.local or DOMAIN\%username% format, where "DOMAIN" or "domain.local" need to be replaced with the domain name or removed if needed )
► If you decide to allow self-enrollment, make sure "Allow ldap enrollment" parameter is enabled. In the same section, you can also allow re-enrollment and modify the intro text of the LDAP web enrollment page.
Cisco Catalyst 3750 series switch
Once the TOTPRadius appliance has been configured , the following steps outline how to configure Catalyst 3750 series switch
to use TOTPRadius as Radius server. Cisco switches have poor functionality in web interface , that’s why we use command shell to give settings:
• aaa new-model This command just activates aaa on your router and nothing more.
• aaa authentication login default group radius Exec Access using Radius.
• radius-server host 192.168.99.11 auth-port 1812 key Qwerty123321Aa
You can use command do show running-config to be sure that new settings are added to configuration.
The following settings are needed to activate ssh . You can skip if you already have them.
• hostname cisco3750
• ip domain-name token2.local
• crypto key generate rsa modulus 1024
• ip ssh version 2
• line vty 0 15
- transport input ssh
- login authentication default
Generate or set the second factor for the user on the TOTPRadius appliance
Second factor for the user can be added in two ways:1) By self-enrollment. Users can enroll their hardware tokens themselves using link http://(totpradius server_ip)/ldap-enroll :
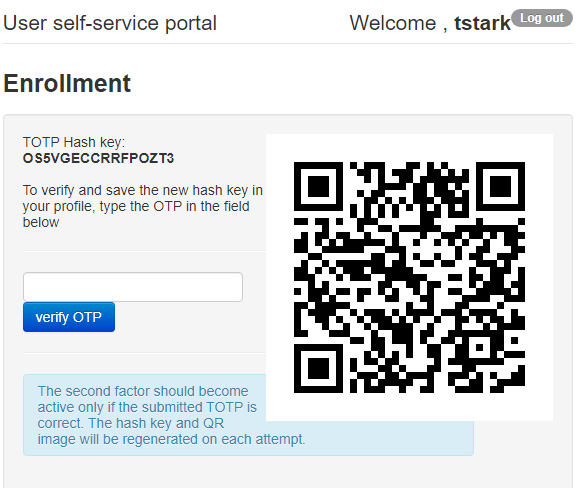
Self Enrollment is possible using any TOTP app (such as Google Authenticator or Microsoft Authenticator). If you wish to use our programmable hardware, you can burn the secret onto the hardware token by scanning the QR code using one of the NFC Burner apps.
2) By TOTPRadius admin. Login to TOTPRadius admin interface, and click on New User:
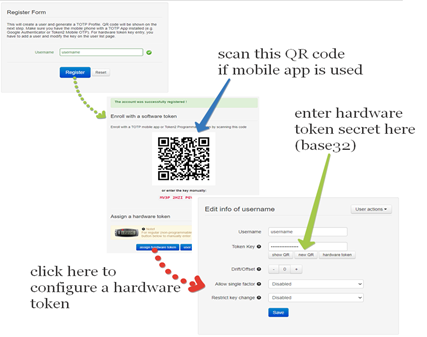
You should now be ready to log in
After all 3 steps above are completed successfully and without errors, the user can login to Cisco Switch
using AD password and the 6 digit OTP generated by the hardware token using PuTTY or other ssh client app:
login as: tstark
[email protected]'s password: Pa$$w0rd123456
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
