Using Token2 FIDO Security Keys for Joomla
 Joomla 4 introduced the possibility of logging in to your website through Web Authentication (WebAuth for short). WebAuthn is the W3C Web Authentication method and allows you to implement a passwordless login using a FIDO2 or FIDO U2F authenticator.
Joomla 4 introduced the possibility of logging in to your website through Web Authentication (WebAuth for short). WebAuthn is the W3C Web Authentication method and allows you to implement a passwordless login using a FIDO2 or FIDO U2F authenticator.Though you still need to provide your username. It uses strong cryptography in a manner that is extremely resistant to the most common problems with passwords: Someone guessed it (brute force attack), someone intercepted it (man in the middle attack), someone tricked you into divulging it (phishing attack), someone cracked it after getting hold of a copy of your database data (SQL injection attacks), or someone stole it.
WebAuthn is not just secure; it is also user friendly! You no longer have to remember long passwords or use a password manager. All you need is an authenticator, and our Fido2 security keys can act as such authenticators.
Please note that the WebAuthn tab in the user profile editor and the WebAuthn login buttons will only be displayed if the user is accessing the site over HTTPS.
In this guide, we will show how to use Token2 security keys for Joomla passwordless authentication .
Requirements:
• Joomla 4 with HTTPS access (a valid, trusted certificate needed)• Admin access to enable security keys (not required if security keys are already enabled)
• Modern browsers support security keys
• A Token2 FIDO security key
Enable passwordless authentication
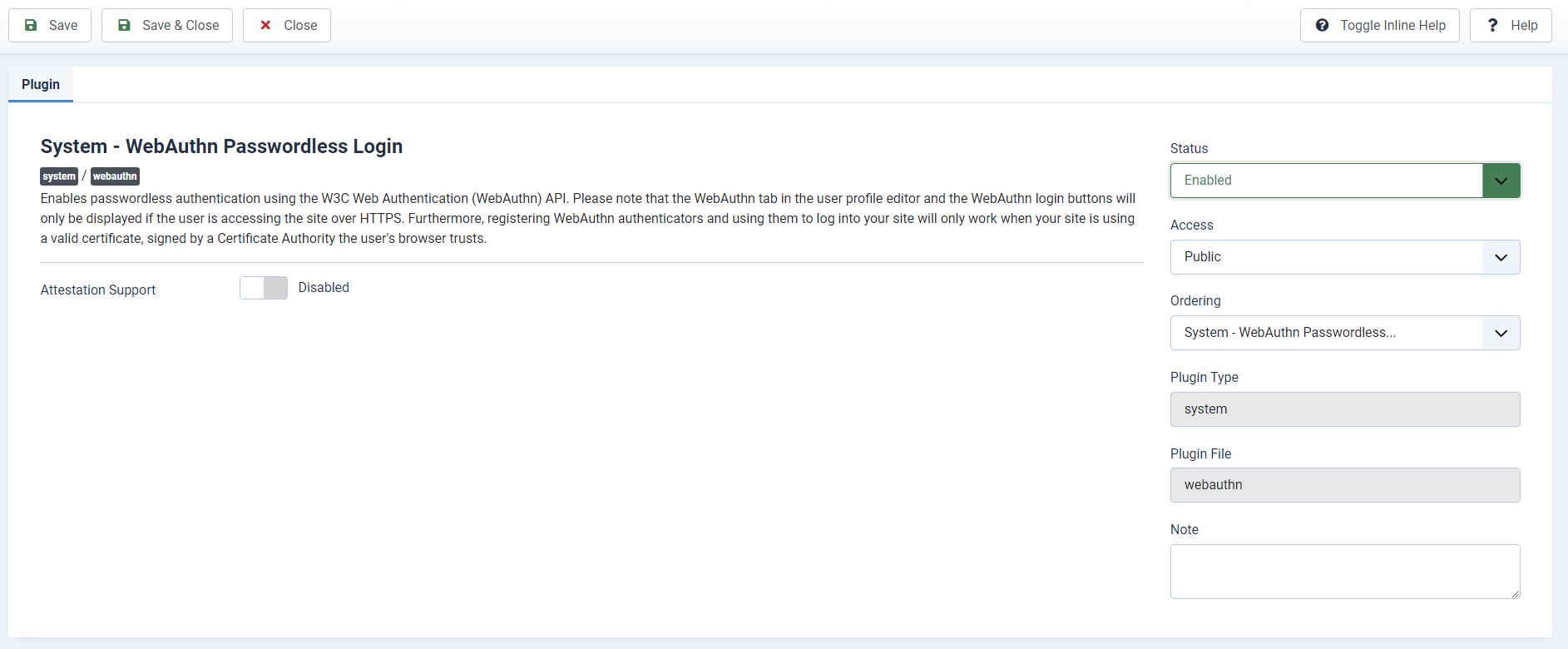
1) From the System Dashboard area, click on Plugins.2) In the search box, type WebAuthn; then, press Enter.
3) Click on the System – WebAuthn Passwordless Login plugin.
4) Enable the plugin by changing its Status to Enabled, and click on Save & Close.
User Configuration
It is important to note that you can only register or remove authenticators on your own user account. For security reasons, even a Super User is disallowed from registering, editing, or adding authenticators to other user accounts.The user must first register with a normal Username and Password. After logging in, go to the User Profile form. For an Administrator:
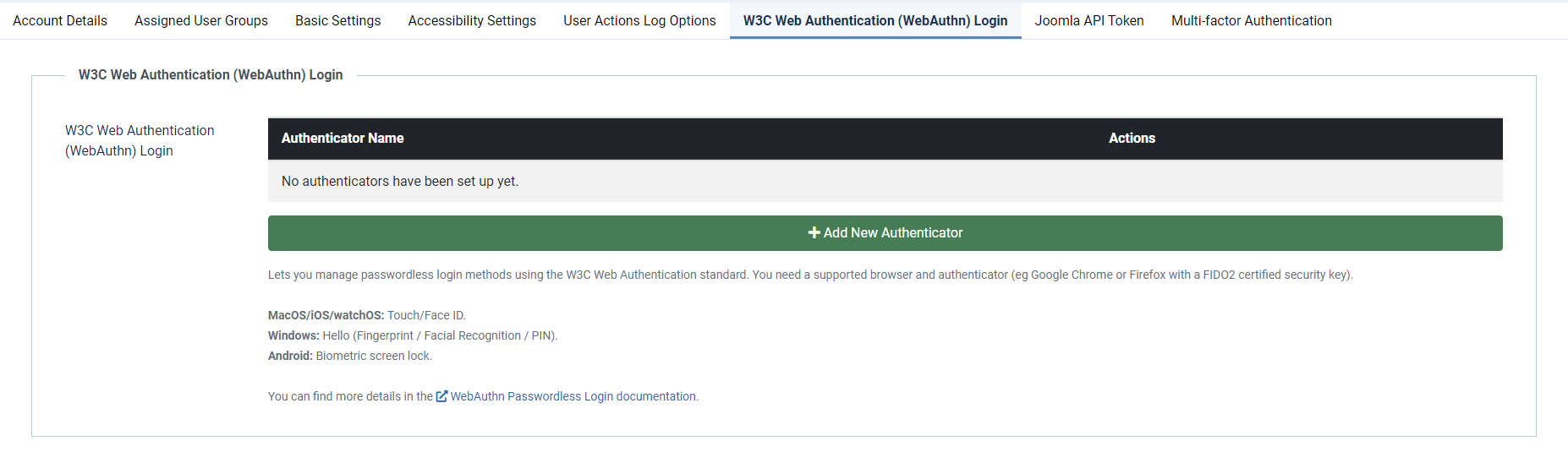
• Select User Menu → Edit Account → W3C Web Authentication (WebAuthn) Login to bring up the form, initially with no authenticators registered.
• Select Add New Authenticator.
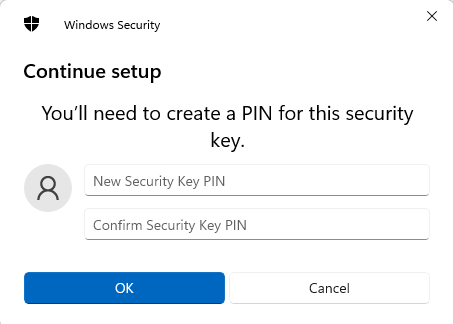
• Joomla will start to identify the inserted security key. If the PIN on the security key was set before, you will be prompted to enter the PIN. Otherwise, you will have to set up a new PIN.
• Press the button on the security key to complete registration.
Note: Security keys differ in the exact instructions to activate them. Your key may require a tap or button press to activate registration.
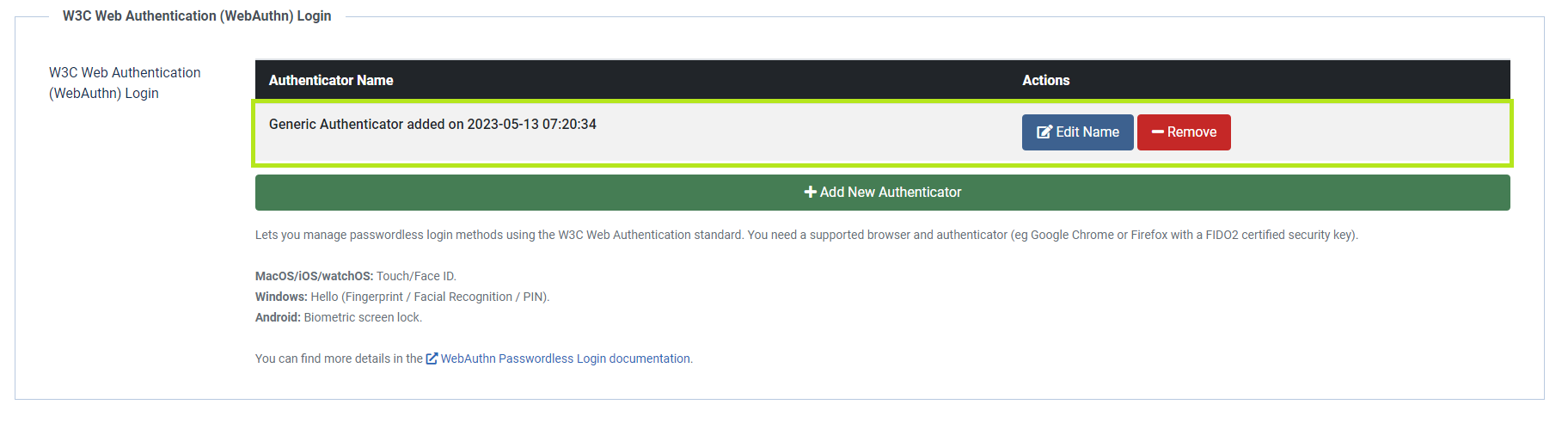
• You can give a friendly name to your registered security key by clicking "Edit Name"
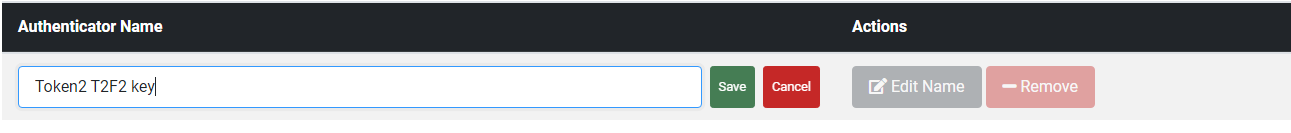
Now your account is ready to use Passwordless.
Authentication
To login, you must enter your username in the login form's Username field. You do not need to enter your password, but if your browser enters it for you just leave it.The password is not sent to the server when the form is submitted via the Web Authentication button.
It follows that you can login with either your Username and Password or Username and Web Authentication.
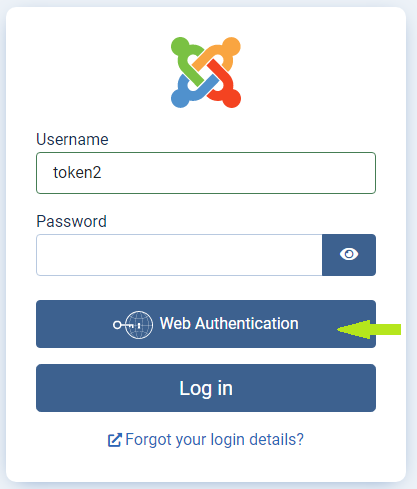
Web Authentication as an MFA method
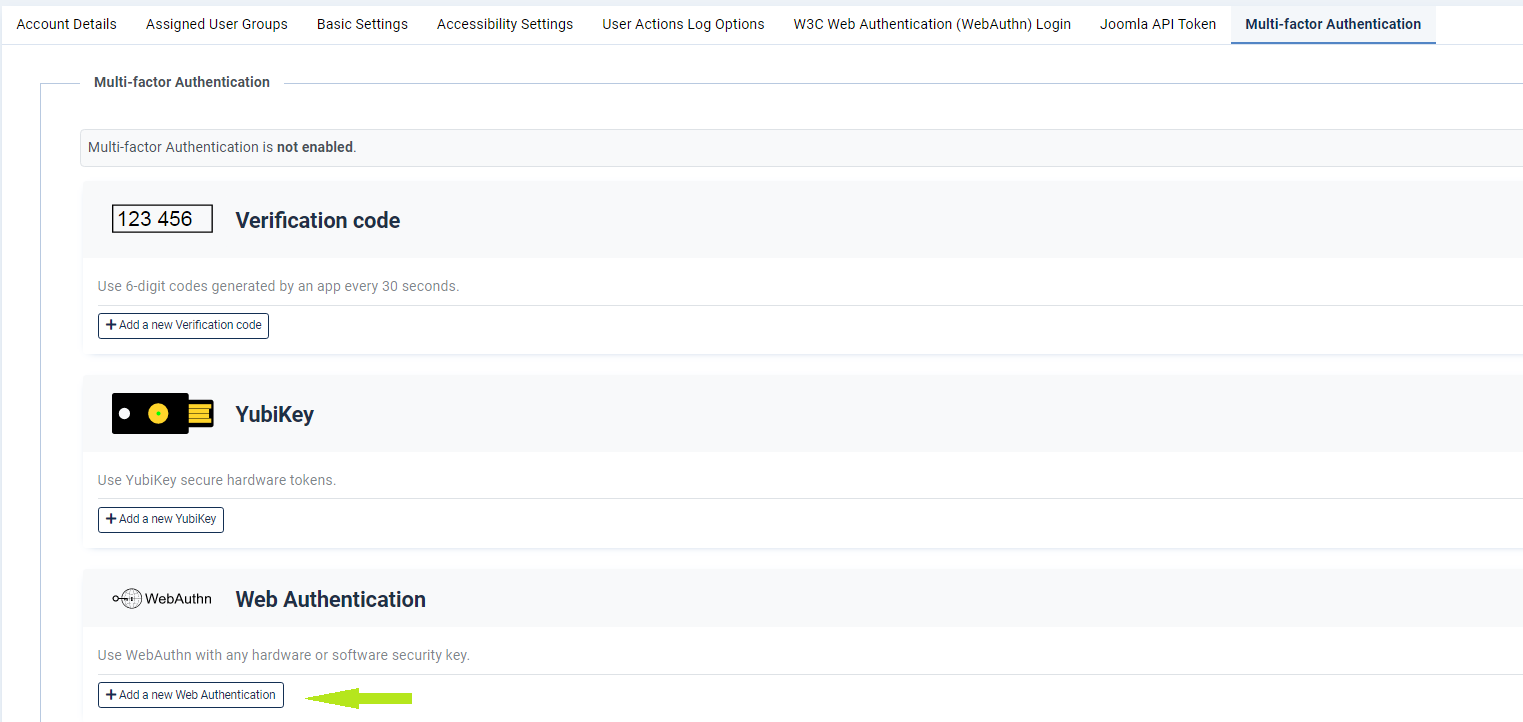
You can also use Token2 security keys as a Multi-factor Authentication method by enabling the Multi-factor Authentication - Web Authentication plugin.Go to User Menu → Edit Account → Multi-Factor Authentication →Add a new Web Authentication to add this 2FA method for user. The enrollment process is similar to WebAuthn Passwordless.
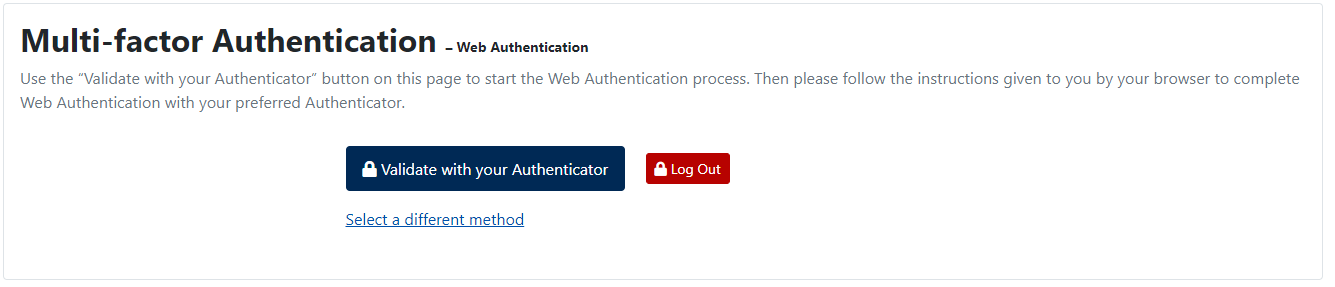
After the standard authentication with your Username and Password, you will be prompted for additional validation with your security key. Insert the enrolled security key, click on Validate with your Autheticator, enter the PIN and press the button on it.
Administrators can only remove MFA options for other users. As a privileged user, you can only remove MFA options from other (non-Super Users) user accounts, or disable their MFA completely.
You cannot edit their MFA configuration or enroll in new MFA methods.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!

