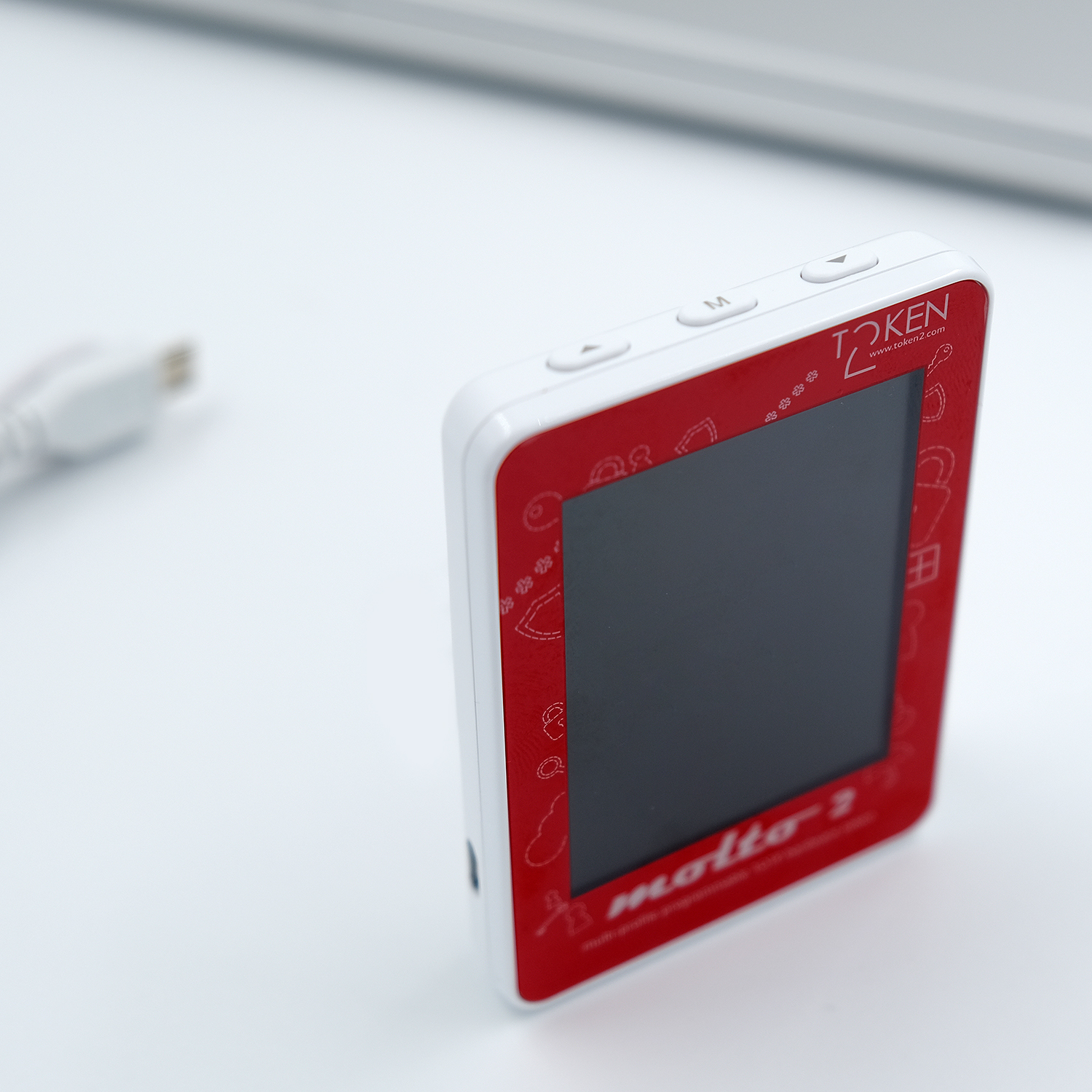
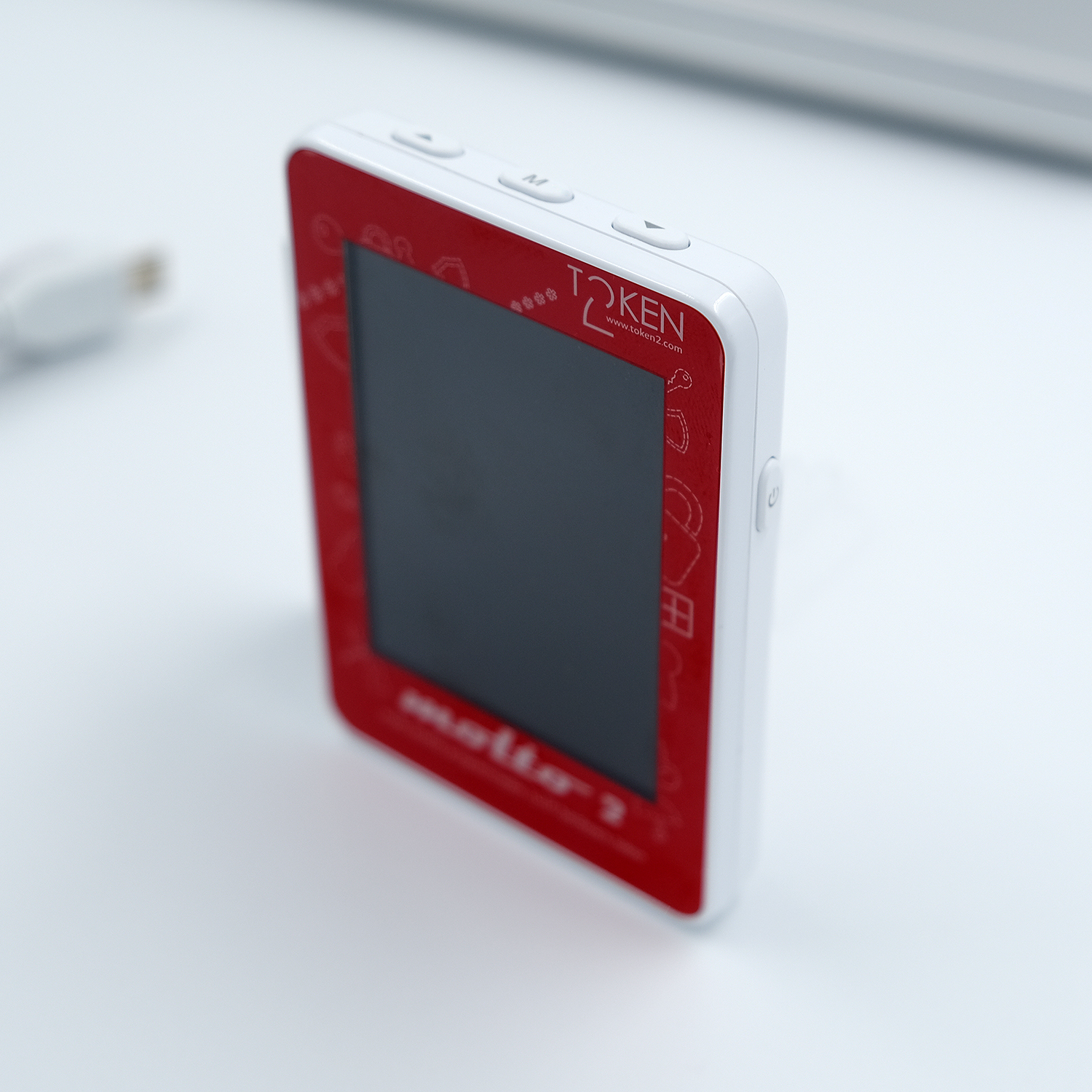
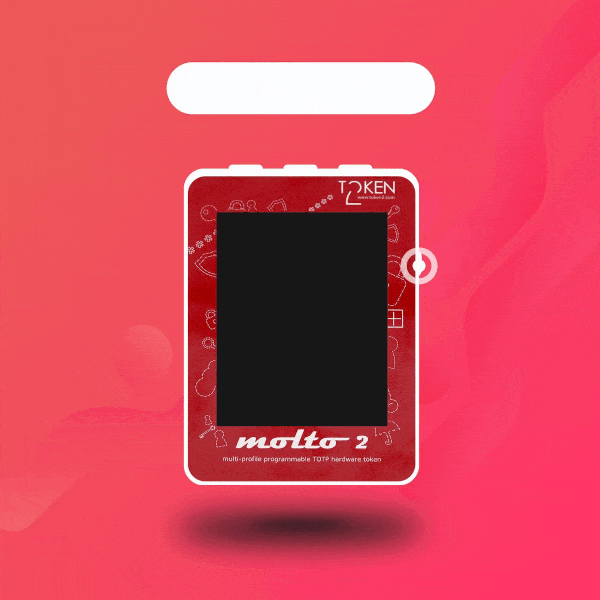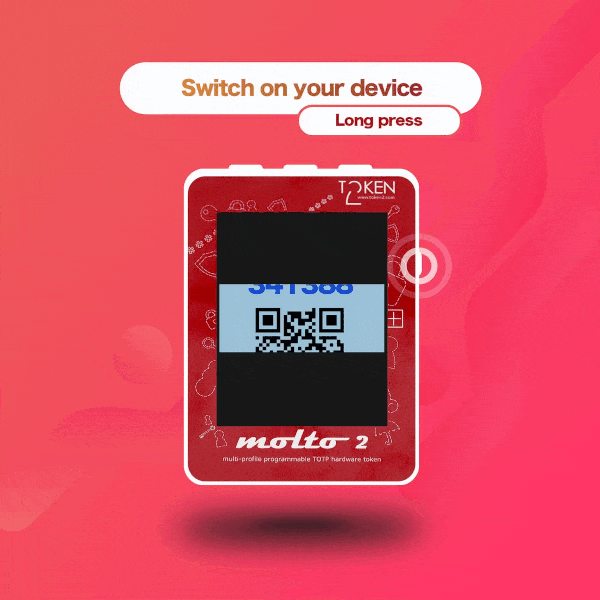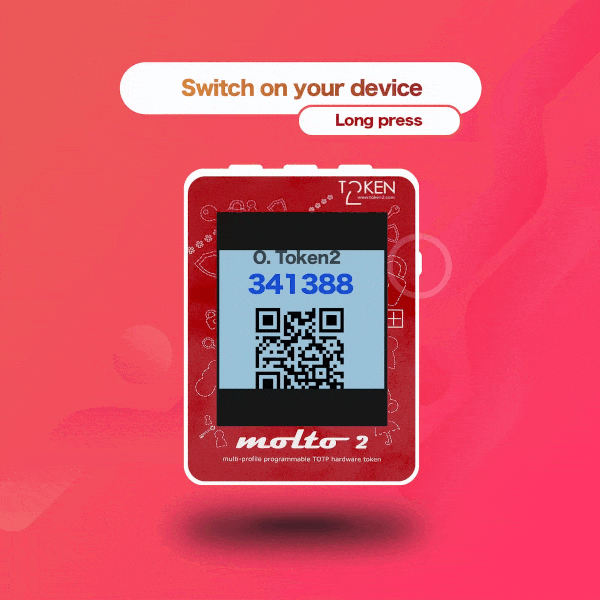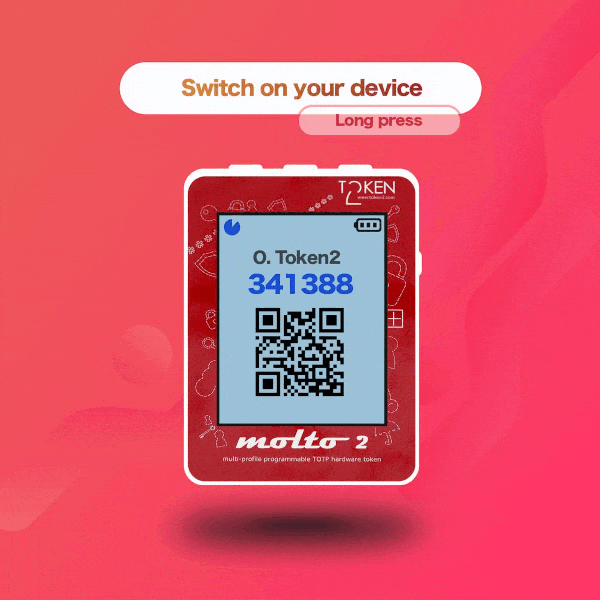
Buy options
€43.00| Model Number | Molto-2 v2 |
|---|---|
| Form-factor | Cuboid with a TFT Screen |
| Functions | TOTP configurable |
| Dimensions | 74×53×12.9 mm |
| Weight | 40 gr |
| Programmable |
100 profiles config protection password HID/Keyboard emulation |
| Product ID | T2-72 |
| Wordpress | fully compatible | |
|---|---|---|
| Google Account | fully compatible | |
| Azure On-Prem MFA Server | fully compatible | |
| Azure Cloud MFA / Office 365 AD Premium P1 or P2 | fully compatible | |
| Azure Cloud MFA / Office 365 AD Free/Basic | fully compatible | |
| Stripe Dashboard | fully compatible | |
| Meraki Dashboard | fully compatible | |
| ISDecisions UserLock | fully compatible | |
| ESET Secure Authentication | fully compatible | |
| Watchguard AuthPoint | fully compatible | |
| Duo | fully compatible | |
| WebUntis | fully compatible | |
This list is far from complete; we only highlight some featured supported systems. Listing all compatible systems would make the list very long. Check with us for more details: |
contact us |
|
If the system you are using is not included in the compatibility list, it does not necessarily indicate incompatibility. We encourage you to refer to our integration guides page or get in touch with us for more information. | ||
Please check product and platform compatibility before placing an order
All pictures shown are for illustration purpose only. Actual product may slightly vary due to product enhancement or other reasons.

Device lock feature new
Starting from Molto2 v2.1 there is a possibility of locking the screen using the "Lock" button in the Windows app or using--lock argument of the molto2.py script. This will hide the OTPs from device's screen until unlock button is clicked or molto2.py --unlock command is issued.
SySS Certified Product
Molto2 has received a 'Certified Product' badge from an independent third-party security assessment conducted by SySS GmbHA revised version of our popular multi-profile USB-programmable TOTP hardware token that can now hold up to 100 TOTP accounts. The profiles can be provisioned/configured via USB using one of our Molto-2 USB Config tools. Molto-2-v2 also has additional features such as OTP shown as a QR image and HID/Keyboard emulation feature.
▣ RFC 6238 compliant
▣ supports up to 100 accounts/profiles
▣ USB-programmable with the USB Config tool
▣ USB keyboard emulation (USB cable included)
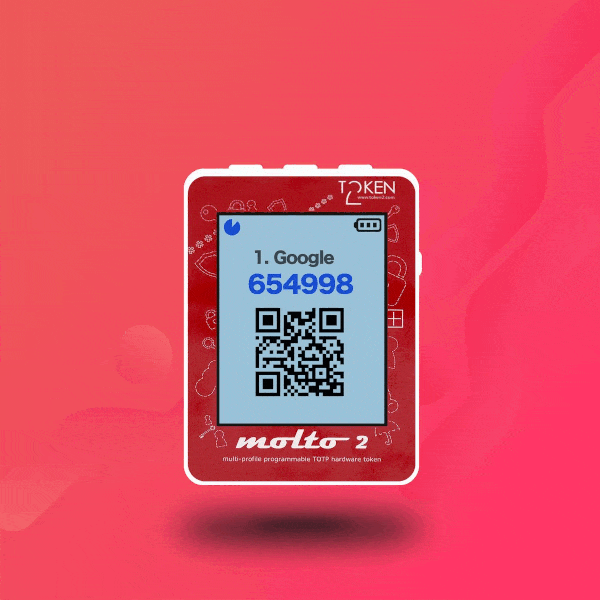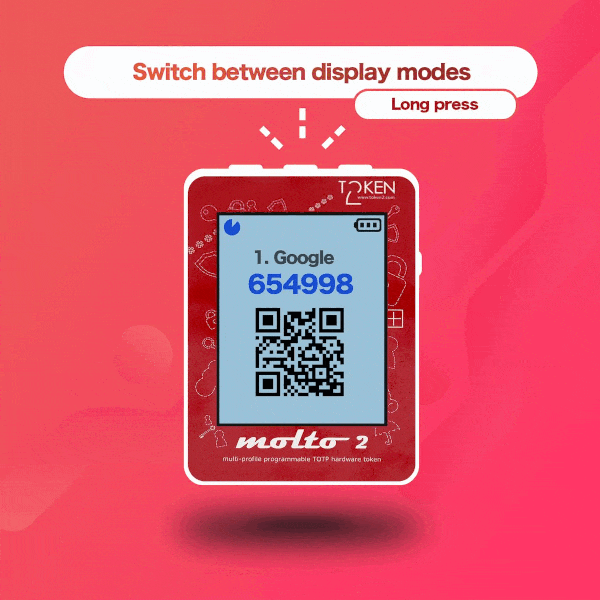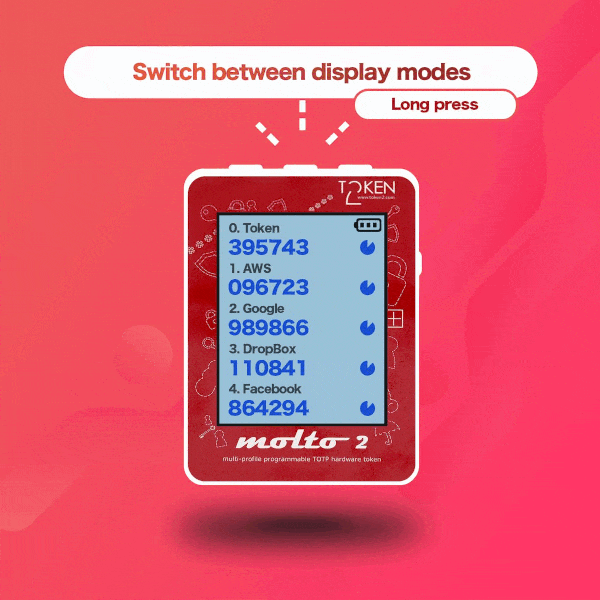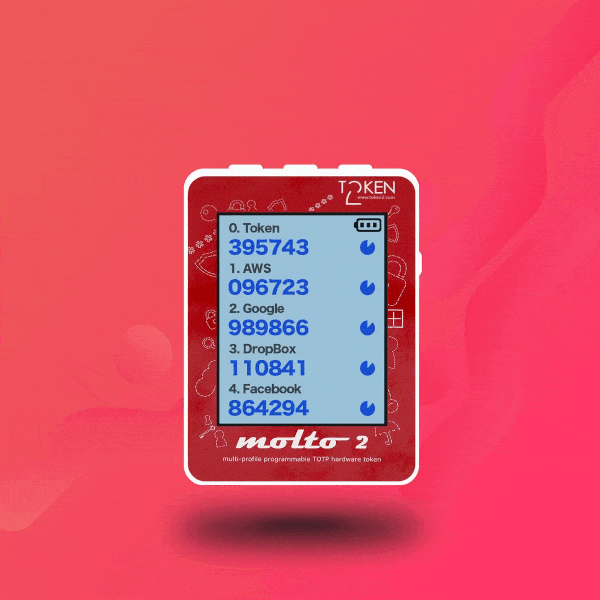
▣ Two display modes: with one TOTP profile per screen and with five TOTP profiles per screen
▣ RTC battery life: 8 years
▣ LCD screen battery: 3-4 months (rechargeable)
▣ Designed, engineered and programmed in Switzerland
Specifications
| Dimensions | 74x53x12.9 mm |
| TOTP Profiles | up to 100 |
| Programmable | via USB, Windows app or cross-platform Python script |
| Time sync | Yes1 |
| Time step | 30 or 60 seconds |
| Hash algorithm | SHA1 or SHA256 |
| Protection |
• Configuration password • Screen security lock feature (v2.1 or newer) |
| OTP Length | 4, 6, 8 or 10 digits |
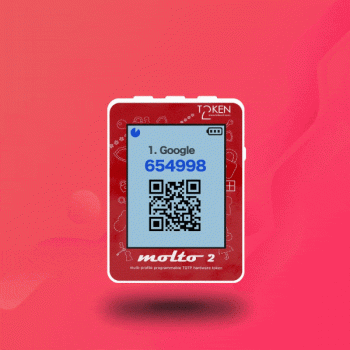
| OTP Entry | Manual, HID-emulation2 or by scanning QR code3 (in Mode1 only) |
1 - Time synchronization is performed using one of the USB configuration tools. The expected time drift is between 1 and 30 seconds per year (depending on ambient temperature), and a periodic sync of the system clock may be required (i.e., every 1 or 2 years, depending on the drift tolerance of the authentication system).
2 - HID functionality will allow sending the current OTP via keyboard emulation when connected over USB. Instead of entering the OTP manually, pressing the 'M' button is sufficient.
3 - The current OTP will be displayed as a QR image. This is useful when automating OTP entry on a different system (e.g., a mobile app) to avoid typing errors. An example where this is particularly useful is EVV (Electronic Visit Verification).
Migrate from mobile apps
Token2 programmable hardware tokens can be used as drop-in replacement of TOTP mobile apps. Token2 has developed solutions to migrate from apps like Google Authenticator and Authy to any of our hardware tokens (or mobile apps).Functionality overview

Starting September 2025, all Molto2 devices will come with a USB-C port only, in accordance with Directive (EU) 2022/2380.
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.